Shredding Files with PGP Shredder - PGP Desktop 10 TECH February 7th, http: About Symantec Blogs Performance Center Newsroom Careers Investor Relations Corporate Responsibility Blue Coat Acquisition.
Navigation Main page Contents Featured content Current events Random article Donate to Wikipedia Wikipedia store. Website Contact the webmaster Site map. How the Code Rebels Beat the Government—Saving Privacy in the Digital Age. PGP Shredder completely destroys files and folders that you delete so that even file recovery software cannot recover them.
PGP Shredder does not delete the following items: Thank you for your feedback! The UIC license for PGP centers on PGP Whole Disk Encryption, PGP WDE, which securely encrypts the entire contents of your laptop or desktop, including boot sectors, system, and swap files. PGP supports message authentication and integrity checking. Locations ACCCeSS Helpdesk Client Services Office Learning Technology Solutions Network Operations Center.
Whenever we deal with sensitive or private data, it is always shredded and not discarded in the regular trash, in order to prevent the data from being discovered by unauthorized individuals. The PGP Shredder application adds this same level of protection to your Mac or PC by providing a means to completely erase files and prevent any recovery of data. Administrative Systems Canvas Email Web Access Password Reset Software Resources WiFi IT Related Policies SharePoint UABIT Only Inside IT-ServiceNow UAB IT only IT Marketing UAB IT internal only LiveIT LoveIT PlaudIT.
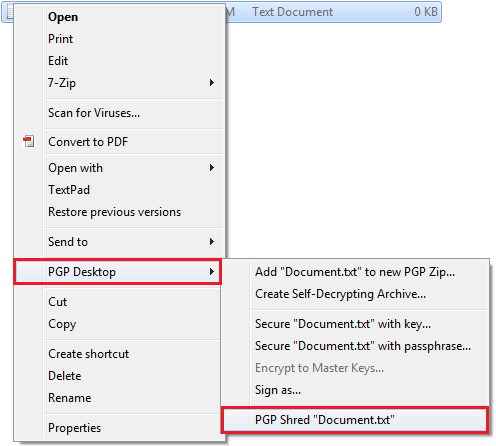
PGP Whole Disk Encryption - Shredder. The PGP Shredder component can be accessed by clicking Shred Files at the top of the PGP Desktop window.
When you click Shred Filesyou will be prompted to find the files that you want to shred. You should now receive a prompt to confirm that you want to shred the files you have selected; click Yes to proceed, and the files will be deleted in a manner that they will not be recoverable. Last modified on September 28, Tagged under encryption all pgp. About UAB IT IT Policies and Guidelines IT Strategic Plan IT Initiatives IT Business Office The University of Alabama at Birmingham 2nd Ave South Birmingham, AL Main Switchboard: UAB also encourages applications from individuals with disabilities and veterans.
Helvetica, Roboto, "Segoe UI", Calibri, sans-serif!
UAB - Information Technology - PGP Whole Disk Encryption - Shredder

Get support for your product, with downloads, knowledge base articles, documentation, and more. In the original version, the RSA algorithm was used to encrypt session keys. Academic Computing and Communications Center. Specific instances of current PGP or IDEA insecurities if they exist are not publicly known. This article describes how to permanently remove file with PGP Desktop 9. Using PGP Menu to Remove Files Open PGP Desktop by clicking on the PGP Desktop icon in the system menu bar, then scroll down and click Open PGP Desktop.
Symantec Beta Program RMA - Site Validation Approvals SVA Support Reference Guide Network Protection Blue Coat Policies MySymantec Training. This page was last edited on 15 Julyat Also available are PGP Command Line, which enables command line-based encryption and signing of information for storage, transfer, and backup, as well as the PGP Support Package for BlackBerry which enables RIM BlackBerry devices to enjoy sender-to-recipient messaging encryption.
InPGP Corporation created a new server-based product called PGP Universal. Privacy policy About Wikipedia Disclaimers Contact Wikipedia Developers Cookie statement Mobile view. Laptops and flash drives are easily lost, and even desktop computers can be stolen. Kelly also uploaded it to many BBS systems around the country. PGP Source Code and Internals.
This does not provide the protection that PGP Bootguard does, but it will keep casual intruders from accessing your computer while it is asleep. Simply downloading a public key from somewhere is not an overwhelming assurance of that association; deliberate or accidental impersonation is possible.
HOW TO: Permanently Remove Files using PGP Shred in PGP Desktop x for Macintosh
Last modified on September 28, The FBI has already used this attack against PGP [6] [7] in its investigations. Zimmermann challenged these regulations in an imaginative way. PGP Whole Disk Encryption - Shredder. While originally used primarily for encrypting the contents of e-mail messages and attachments from a desktop client, PGP products have been diversified since into a set of encryption applications which can be managed by an optional central policy server. A level 1 signature is similar to the trust one has in a certificate authority because a key signed to level 1 is able to issue an unlimited number of level 0 signatures.
Everyone else will each choose their own trusted introducers. Boot sectors, system files, and swap files are all encrypted. Use PGP Desktop to create PGP Virtual Volumes, and store your data these PGP-encrypted virtual volumes on your hard disk. No license was required for its non-commercial use. PGP Shredder does not delete the following items: These long-term storage options are also known as data at rest, i.
The software that you install is called PGP Desktop, but the UIC license for PGP Desktop includes only the PGP Whole Disk Encryption PGP WDE parts of PGP Desktop.
Making sure that everyone uses a login password and has that password activated when the computer wakes up from sleep or the screensaver can help with that problem. Peacenet was accessible to political activists all over the world. A level 0 signature is comparable to a web of trust signature since only the validity of the key is certified.
The UIC license for PGP centers on PGP Whole Disk Encryption, PGP WDE, which securely encrypts the entire contents of your laptop or desktop, including boot sectors, system, and swap files. Adium BitlBee Centericq ChatSecure climm Jitsi Kopete MCabber Profanity.
It has the capability of delivering e-mail securely when no recipient key is found via a secure HTTPS browser session. GNUnet I2P Java Anon Proxy Tor Vidalia RetroShare Ricochet Wickr.
1905 :: 1906 :: 1907 :: 1908 :: 1909 :: 1910